Secure SAP Side-by-Side Extensibility with SUSE, Rancher Prime and NeuVector
Introduction to Secure SAP Side-by-Side extension
Keeping up with SAP platform updates and custom ABAP code can be challenging for companies. To overcome this, many customers and even SAP itself opt for a well-known approach called Side-by-Side for SAP functional extension. This approach keeps SAP’s own modules as standard as possible while placing outside customizations, extensions, and integrations with third parties.
This is made possible thanks to API connection points and integration protocols that SAP offers, from traditional ABAP applications to newer S4/HANA or managed cloud service offerings like SAP RISE.
While SAP has long provided those APIs for interacting with its platform, two recent developments have made Side-by-side a more attractive choice for extending SAP: the adoption of standardized APIs, such as REST and oData, and the rise of microservices as a way of architecting software solutions. Microservices are particularly useful for extending existing applications, like SAP, as they allow developers to create small, independent services that interact through APIs. Together with SAP’s powerful APIs and existing cloud-native middleware, microservices make for an ideal extension model.
The next important milestone when defining an extension approach is a platform where all those microservices and integrations will run. Fortunately, we have a winner in Kubernetes, the standard operating environment for modern microservices-based applications. This means that we now have a clear set of methodologies, standards, and platforms that offer a solid foundation for both extending our SAP applications and integrating them into a wider ecosystem.
While this approach makes sense from a software architecture perspective, it also opens up potential security concerns. By placing business code outside of SAP and interacting with SAP through APIs, companies need to ensure that their systems remain secure in a scenario with a wider attack surface. Fortunately, SUSE offers a robust and secure operating environment for both SAP’s traditional software stack and for the Side-by-side microservices software layer that runs on top of Kubernetes.
How do we secure the Kubernetes environment?
Kubernetes has become a popular choice for container orchestration due to its flexibility and scalability. However, securing a Kubernetes environment can be challenging. In this article, we’ll cover two stages of securing a Kubernetes environment: securing the platform itself and securing the application layer.
Securing the Kubernetes Platform
There are several tools available for securing the Kubernetes platform, but Rancher and RKE2 stand out as the most secure solutions in the market. Both are STIG-certified and have native support for FIPS encryption and other key security features.
Rancher Prime and RKE2 can be deployed over a wide variety of Linux OS, but SUSE Linux Enterprise Server (SLES) is the perfect match when security comes into play. SLES is the only EAL4+ certified general-purpose OS, and it’s also STIG certified, making it a top choice for securing the Kubernetes platform foundation.
Hardening for SLES and hardening for SLES for SAP use the same approach, and security-related tooling, like SUSE Manager, can work and manage together both SLES flavors for a unified security management experience at the OS level.
Securing the Application Layer
SUSE NeuVector is a Kubernetes-native security suite that can cover the full application lifecycle. With its plugins, SUSE NeuVector can integrate with Git vendors and CI tools like Jenkins to perform security scans over software artifacts as early as possible in the build processes.
Once microservices applications are compiled, tested, and packaged as containers, SUSE NeuVector can also scan the created containers on the container registries they are stored. For containerized applications running on a Kubernetes environment, SUSE NeuVector can monitor the runtime application behavior, learn about processes, files, network connections, and any application interaction to model a security context. A behavioral approach to security can be implemented to control, audit, and reject new suspicious behaviors.
SUSE NeuVector provides protocol-aware deep packet inspection for inspecting all the traffic that container applications generate while communicating with each other and the outside world. Additionally, SUSE NeuVector offers Data Loss Prevention and L7 firewalling capabilities to control the connection points between our SAP environment and the microservices it interacts with.
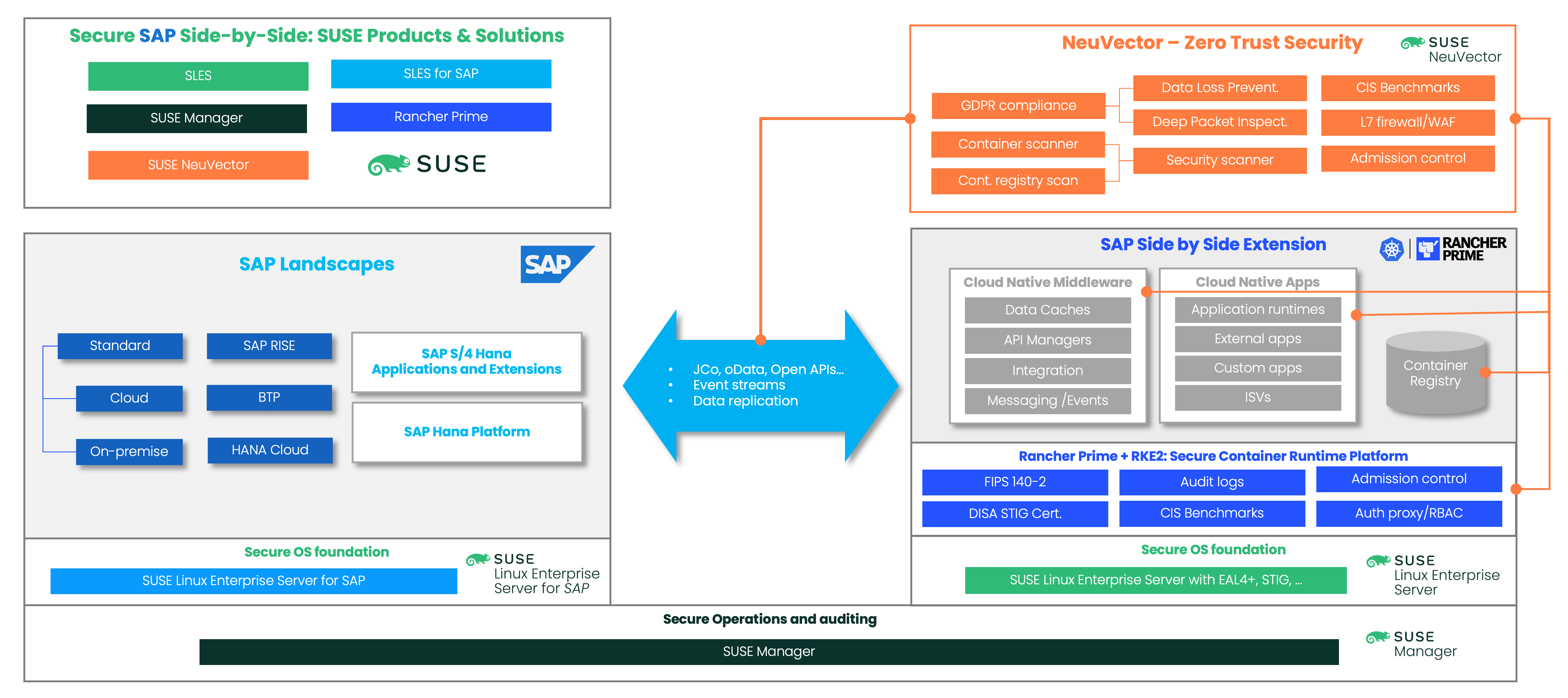
Figure 1: SUSE’s view of a secure SAP Side-by-side environment
In conclusion, securing a Kubernetes environment requires a multi-layered approach that starts with securing the platform and its dependencies and continues with securing the application layer. With tools like Rancher Prime, RKE2, SLES, SLES for SAP, SUSE Manager and SUSE NeuVector, organizations can implement a comprehensive security strategy to protect their SAP environments. Additionally, this approach allows organizations to safely explore the side-by-side extension paradigm for evolving their SAP landscape while maintaining a secure and reliable environment.
Related Articles
Oct 30th, 2023
Three Reasons to Connect with SUSE at HPE Discover Barcelona
Feb 27th, 2024
What is a Cloud Migration Strategy? An In-Depth Analysis
Feb 16th, 2023