Confidential Computing. Enabling Enterprise Innovation While Securing Your Data
This blog will discuss the challenge of maintaining data security, sovereignty, and compliance. This discussion has evolved with the growth of multi-tenant environments and the widespread use of public cloud services, which has brought about new challenges in data security. We will explore the significance of Confidential Computing and how it addresses the concerns of data breaches and its vital role in safeguarding sensitive information and ensuring compliance with local regulations.
Introduction
As the digital landscape evolves, data security is becoming increasingly important. Enterprises worldwide face the complexity of protecting sensitive information. At the same time, data sovereignty has become a popular term and is concerned with the rise of IT, which has moved out of the local data center and begun to spread across the globe with the increasing adoption of public cloud.
How can we ensure data sovereignty and safety? Also, how can I ensure compliance with local norms and regulations while minimizing liability? These questions are hurdling enterprise innovation and retraining the adoption of new technologies.
Challenges in Modern Data Security
Traditionally, data security measures have relied on encryption techniques to safeguard data stored on physical media (data at rest) and data transmitted over networks (data in transit). These measures ensured that unauthorized actors could not access sensitive information, even if they managed to intercept it. However, the rise of multi-tenant environments and the widespread adoption of public cloud services have introduced new challenges. In these settings, memory and processors are shared resources, making it crucial to protect data while it is being processed or in use.
A data breach occurs when an unauthorized actor accesses your data or, even worse, is able to change it; thus, to safeguard the data, the focus is on the shared resources in which your data can be accessed. Hence, traditional data security measures were founded on encryption at rest and in transit to safeguard data. With a focus on storage and the network, enterprises ensured that data couldn’t be accessed by unauthorized actors. However, with the rise of multi-tenant environments, especially with the public cloud, memory and processors have become shared resources, and data in use has become a big concern.
The Significance of Confidential Computing
Confidential Computing (CoCo) is about data security and compliance, focusing on protecting data anywhere, not just at rest or in transit but also during its active use. This addresses the concerns of data breaches, where unauthorized actors gain access to sensitive information and potentially cause severe harm to individuals and organizations alike.
A Confidential Computing Environment (CCE) is a secure computing environment designed to protect data in use. It leverages specialized hardware and software technologies to ensure that sensitive data remains protected even while being processed, and it is also essential to have attestation capabilities for compliance assessment. By leveraging technologies such as Trusted Execution Environments (TEEs) and hardware-based attestation, confidential computing provides secure processing where data is encrypted in memory and in the CPU and can be processed without exposure to other system components or external threats. This approach together not only enhances data security but also helps organizations meet stringent compliance requirements by providing verifiable assurances of data protection.
 Confidential Computing Environment secures an enterprise workload based on SUSE Linux Enterprise Server running in a potentially compromised multi-tenant environment encrypting data in use.
Confidential Computing Environment secures an enterprise workload based on SUSE Linux Enterprise Server running in a potentially compromised multi-tenant environment encrypting data in use.
Attestation and compliance
Running encrypted is just one side of Confidential Computing. We still need to trust our environment provider (like our hyperscaler) when he claims that the environment is secure and safe, but it is only a statement without any proof, and compliance assurance needs to be based on evidence.
This is where (remote) attestation starts. Attestation is providing Trust to the Confidential Computing Environment; it is the proof needed by enterprises that data and processes are running in a safe environment. Attestation verifies the integrity and authenticity of the Confidential Computing environment. Hence, it ensures that the code is running in the Trusted Execution Environment and is executing as expected. In order to accomplish this, the process is done with the collaboration of the hardware and operating systems, which certify with a digital signature of both providers that, at this point in time, the operating system is running on the hardware that it is supposed to run on, and is encrypting the data in use. This removes the “blind trust” in the computing environment from the equation.
Enterprises can use attestation as proof that the Confidential Computing environment is secure and, therefore, check it also before sensitive data or workloads are sent to be processed. Furthermore, it can be checked regularly and stored as a compliance assessment.
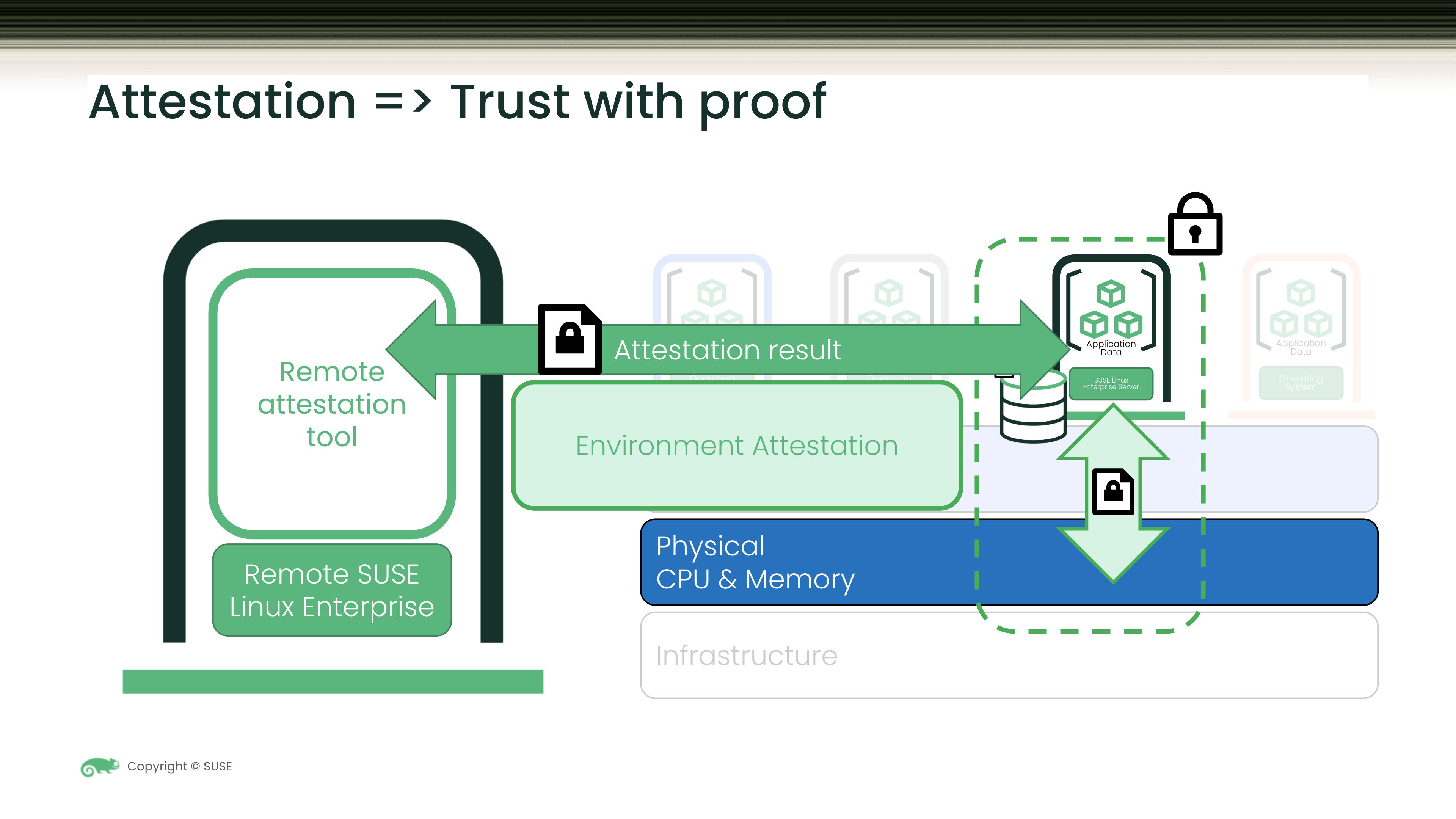 The attestation process ensures the Confidential Computing Environment state of an enterprise workload based on SUSE Linux Enterprise protecting data in use.
The attestation process ensures the Confidential Computing Environment state of an enterprise workload based on SUSE Linux Enterprise protecting data in use.
SUSE’s Commitment to Confidential Computing
We have been discussing what a Confidential Computing Environment and Attestation is and what is needed to leverage it. The answer is simple: a trusted hardware provider that provides a chip ready for a Trusted Execution Environment and a trusted Operating System that enables the operation and is able to provide the tools for the attestation.
At SUSE, we recognize the critical importance of securing data at every stage of its lifecycle. SUSE is committed to the security of our customers, and our solutions are designed to integrate seamlessly with confidential computing technologies, providing enterprises with the highest levels of security without compromising on performance or usability.
SUSE joined the Linux Foundation’s Confidential Computing Consortium, a community focused on projects that deal with securing data in use and accelerating the adoption of confidential computing through open collaboration. Also, SUSE collaborates closely with chip providers, such as AMD, Arm, and Intel, to enable Confidential computing on Linux, which is one of the main contributors in that area.
Leverage Confidential Computing-ready with SUSE Linux Enterprise Server products
SUSE enables the use of Trusted Execution Environments in SUSE Linux Enterprise Server and SUSE Linux Enterprise Micro, supporting and adding a consistent roadmap of support for Intel® TDX and AMD® SEV technologies for guests and hosts.
SUSE Linux Enterprise Server also works with the Secure Execution technology of IBM Z and IBM LinuxONE systems. For more info about it you can read the Confidential Computing with SUSE Linux Enterprise Base Container Images Using the IBM Hyper Protect Platform webpage.
First, SUSE is providing fully supported, Confidential Computing-enabled SUSE Linux Enterprise Server instances on the marketplace of Confidential Computing hyperscalers like Microsoft Azure, with its new Intel TDX-based instances, or Amazon Web Services Nitro Instances or Google Cloud, with its AMD SEV-ready environments.
SUSE Linux Enterprise Server and SUSE Linux Enterprise Micro are also adding capabilities to run as a Confidential Computing-ready virtualization host platform with KVM to enable enterprises and MSPs to create their own private Confidential Computing-ready environments based on Linux virtualization.
Furthermore, thanks to the new hardware capabilities, SUSE Linux Enterprise Server optimization minimizes the impact of Confidential computing performance, making any workload leverage a more secure processing environment with negligible impact on performance.
Confidential Computing-ready Attestation with SUSE Manager
As a step forward in the enterprise adoption of confidential computing, SUSE is also adding Confidential Computing attestation capabilities to SUSE Manager to ensure compliance. With SUSE Manager’s new attestation capabilities, together with SUSE Linux Enterprise Server and SUSE Linux Enterprise Micro, enterprises can leverage Confidential Computing by proving that the remote environment is running in a Confidential Computing environment for compliance.
Use Cases
- Financial Services: For financial institutions, Confidential Computing is crucial in protecting sensitive financial data during transactions and analytics.
SUSE’s solution helps banks and financial services companies deploy their server in compliance with regulatory requirements and maintain customer trust. - Healthcare: In the healthcare sector, protecting patient data is paramount. SUSE’s Confidential Computing-enabled products ensure that enterprises can run their systems anywhere while sensitive health information remains secure during processing, supporting compliance with regulations like HIPAA.
- Government and Public Sector: Government agencies handle vast amounts of sensitive data that require stringent security measures. SUSE’s solutions provide the software infrastructure to ensure Data Sovereignty, enabling secure data processing and aiding in the protection of national security and citizen privacy.
Conclusion
As organizations continue to navigate the complexities of the digital age, SUSE remains at the forefront, providing innovative and robust security open-source solutions that empower businesses to operate securely and efficiently. Confidential computing is not just another technology; it is mandatory to keep enterprise innovation capabilities while keeping data sovereign.
SUSE’s enhanced portfolio with Confidential Computing capabilities and SUSE’s commitment to improving it provides choice to enterprises, giving freedom to innovate and leverage new environments to any enterprises, including those highly regulated industries that until now can’t use the public cloud for their confidential data.
In conclusion, SUSE’s commitment to Confidential Computing enables enterprises, government organizations, healthcare operations, and Service Providers to use shared computing capabilities in a much more robust and secure way than it has been possible in the past.
This blog post continues the previous one and aims to provide insight into why An Enterprise Linux Platform is the choice for Security and Compliance in IT. Hence, it describes the impact of using a long-term supported Enterprise Linux with certifications from a provider with an evaluated secure software supply chain and its importance in security, compliance, and minimizing liability for using open-source software.
Further technical information can be found on the Confidential Cloud: Introduction to Confidential Computing and SUSE open-sources Secure VM Service Module for Confidential Computing blogs and in the SUSE Linux Enterprise Server and SUSE Linux Enterprise Micro product webpages.
Related Articles
Aug 22nd, 2024